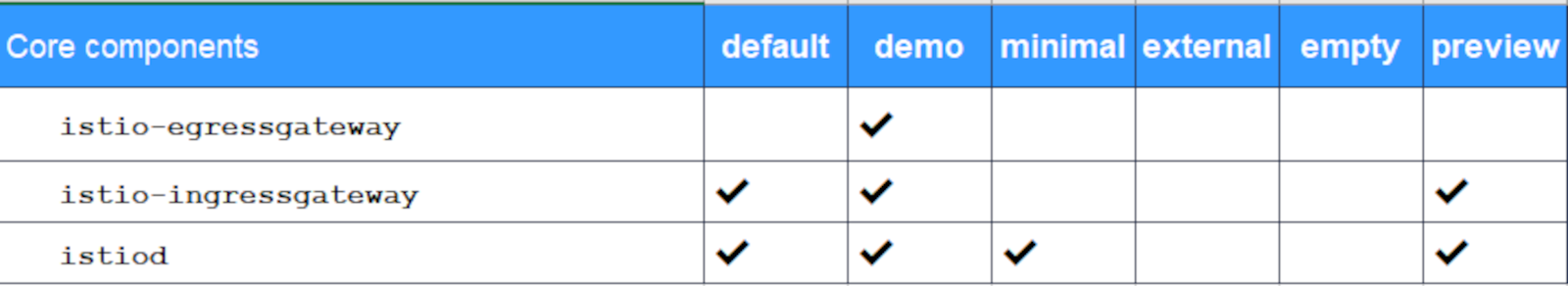
Service mesh
What is Service Mesh and, especially, what is Istio?
Service mesh is a great technology that improves how services communicate in a microservice architecture. A service mesh like Istio can be leveraged for better observability and insights into your microservices. Let’s look at how and why in this blog post.
Go Deeper